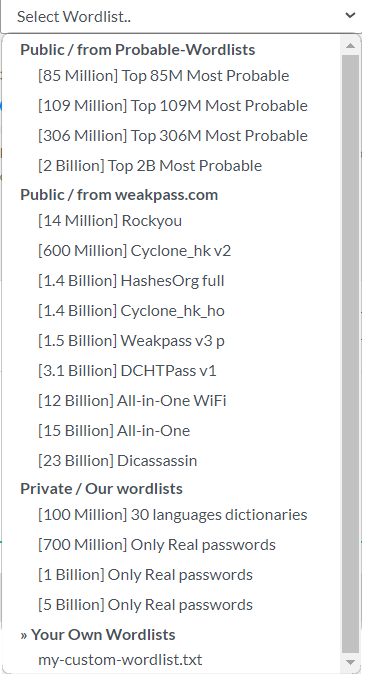
Here are the Wordlists & Bruteforce attacks we offer
Wordlists
We propose several world famous and very efficient Wordlists from public repositories and from our own private collection.
- Probable-Wordlists is a well known Github repo with Wordlists sorted by probability
- weakpass is another well known Wordlists repo
- Our own wordlists collection, a merge of real passwords
- You can also upload your own and custom wordlist to your account, and use it to test your hashes, see Wordlists section.
- Contact us if you want to see other wordlists added to this list
You can also add a Ruleset to your attack, to mangle words and create new candidates. Rules modify, cut or extend candidates to create more passwords.
The attack becomes (far) more efficient.
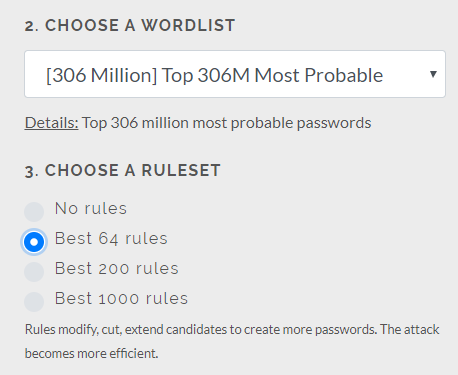
More information about Rule-based attacks.
Bruteforce
Tries all combinations from a given keyspace. It needs a Charset and a Length:
- Charset: can be Lowercase (a to z), Uppercase (A to Z), Digit (0 to 9), Symbols, etc.
- Length: password length
The number of candidates (keyspace) to try is: Number of chars in Charset ^ Length.
The cracking duration is: Keyspace / Hashrate.
Configure a custom Bruteforce attack with your own Charset and Length via our Bruteforce Configurator.
The Summary part shows:
- The chosen Charset (here Lowercase + Digits)
- The chosen Length (here from 3 to 10 characters)
- Number of candidates we will test for you, here: 3,760,620,109,777,728
- Estimated duration of the job, which depends on the previous Charset and Length choices and the algorithm (MD5 in this example).
- Payment is required upfront.
Get more information here.
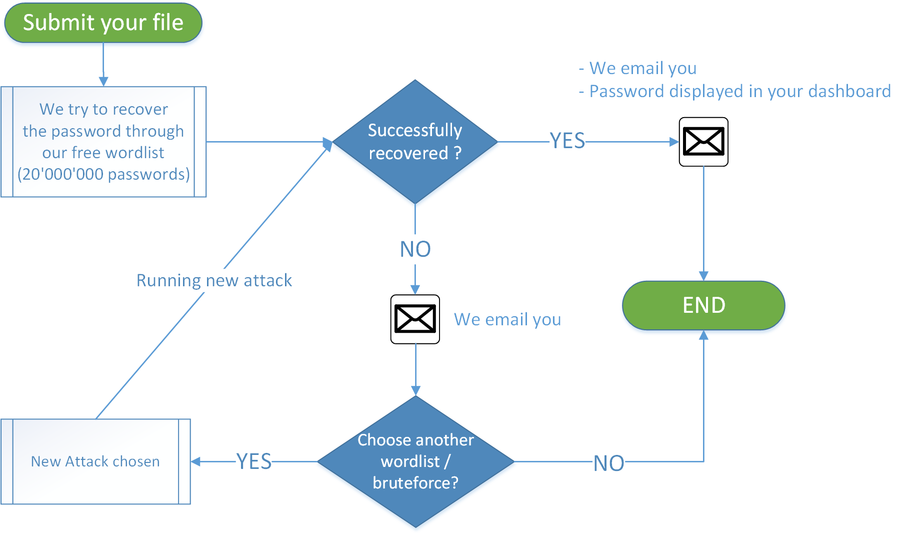
Recovery Workflow