Introduction
What do you think is the cost of cybercrimes in 2024?
It’s a whopping $9.5 trillion. These numbers show the dire need for companies to upgrade their data security.
Similarly, data security must be upgraded to preserve your business's assets. But what powers these cyberattacks?
Generative AI, social engineering, and third-party risks are behind the most sophisticated and convincing attacks.
Third-party risks are further contributing to these attacks. The cybersecurity threats companies face today go beyond securing data; it involves meeting regulatory standards and maintaining stakeholders' trust.
We have conducted in-depth research to provide eight ways to upgrade your data security in 2024.
1. Adhere to data privacy laws
Every day customers share their personal information and data on various platforms. With a data breach occurring every 39 seconds, your customers want you to protect their data from hackers and cybercriminals.
That’s where data privacy laws like the California Consumer Privacy Act (CCPA) and the General Data Protection Regulation (GDPR) come in.
These laws have changed how you manage personal data and information. Today, you cannot use, sell, or process the customer’s information without prior approval. Consent compliance for CCPA is important because it gives customers the right to object to data processing. Customers even have the right to know who collects or sells their data.
They can choose to either give their consent or reject it. Ensuring compliance with every aspect of data privacy laws might be challenging. For this reason, many companies rely on Consent Management Platforms. With these platforms, you obtain user consent, increase consent rates, and build user trust while ensuring compliance with data privacy laws.
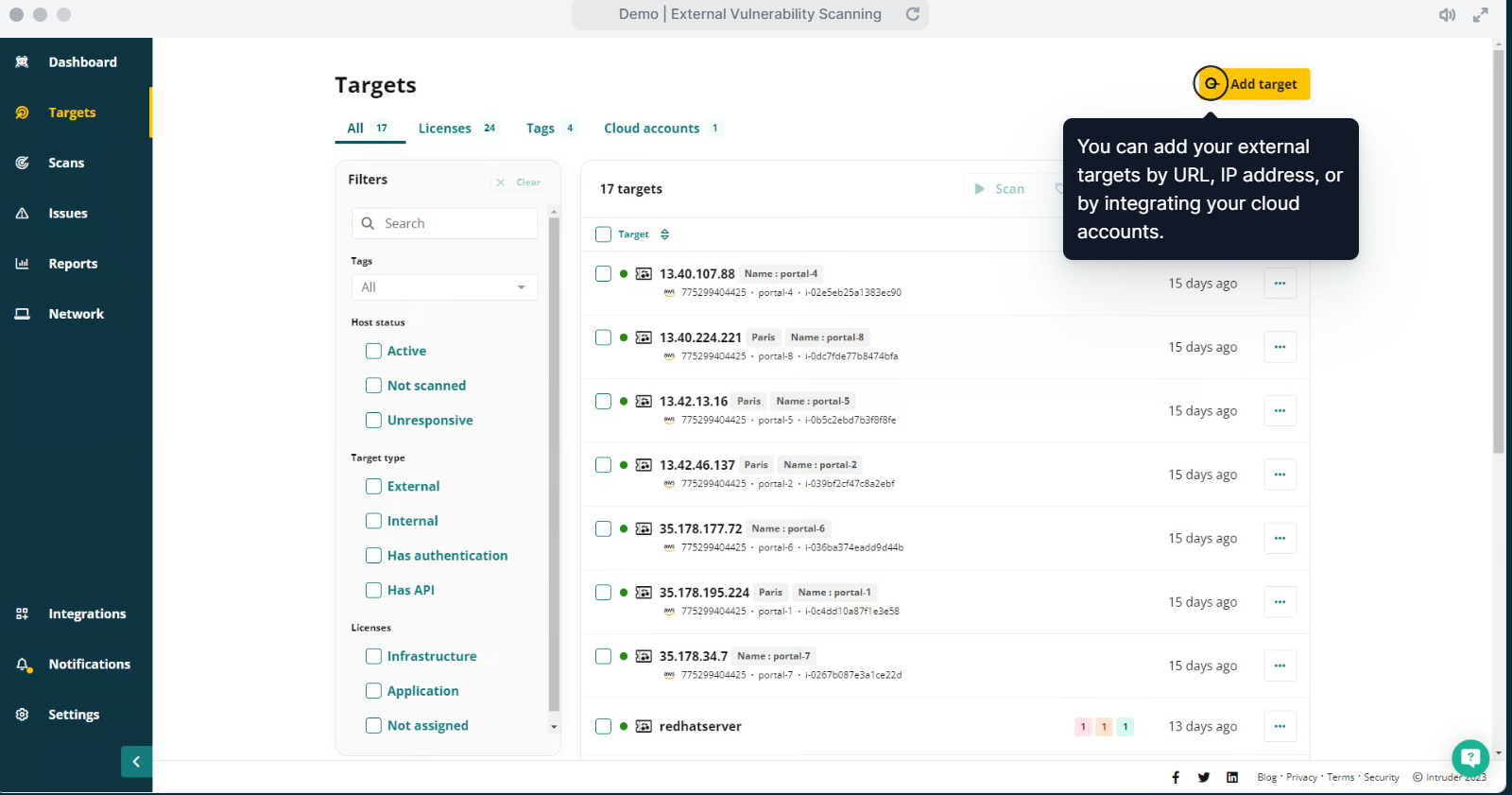
2. Use penetration testing to secure your digital assets
Penetration or pen testing is a popular way of simulating cyberattacks on your systems. It helps you identify weaknesses that hackers can exploit. Pen testing focuses on high-risk vulnerabilities because every vulnerability has a different risk level.
You use real-world hacking techniques, which helps you prepare for similar incidents.
With pen testing, you achieve regulatory compliance with GDPR or Payment Card Industry Data Security Standard (PCI DSS). You can use the following types of pen testing to increase data security:
● Network penetration testing
● External penetration testing
● Internal penetration testing
● Cloud penetration testing
● Automated penetration testing
● Social engineering
● Red teaming
3. Increase your network security
When trying to protect your data, never overlook your network security. Securing your network maintains the integrity of your company's data and ensures your systems are secure. Use these tactics to strengthen your network security and decrease the likelihood of attack.
● Implement robust firewalls to control network traffic. You can install Next Generation Firewalls (NGFs) in your cloud to ensure complete protection. NGFs offer advanced features, such as an Intrusion prevention system (IPS), Stateful protocol inspection (SPI), and container protection others.
● Use VLAN or virtual LANs. VLAN helps you segment the physical network without investing in additional devices or services. For instance, your marketing department has a different segment than an accounting or finance department.
● Update and patch your system to prevent it from the latest security threats.
● Keep your identity and access management (IAM) updated. As a best practice, grant access to users depending on their roles and requirements. This gives rise to IAM, a cloud service controlling unauthorized user access. Regularly review and update your IAM to ensure the right individual accesses the right resource at the right time.
4. Analyze code changes, APIs, and data flows
In 2024, hackers will extend beyond unsanitized data inputs and login forms. Application programming interfaces (APIs) help you transport data into a microservice architecture. Today, more and more companies are using cloud services, and APIs have given hackers more attack surface.
When software applications transport data using an API, tracking every parameter passed via an API is challenging. To prevent this, you should document your APIs manually and keep track of potential code changes. Also, regularly conduct API security audits, which include proper authentication and authorization, ensuring encryption of sensitive data.
It also ensures your APIs are not exposing more information than necessary. You can even rate limits to prevent potential DDoS attacks and prevent abuse.
Another important thing to consider is analyzing data flows. Data flow analysis helps you map the data’s journey from the entry to the exit point. As a result, it becomes easier to identify potential weak points. During data flow analysis, you can discover that data is not encrypted during transit or that your sensitive data is stored insecurely.
Having a clear idea of your API, data flow analysis, and code changes will help you implement security measures to protect your data at each stage.
5. Implement multi-factor authentication (MFA)
Time and again, we have heard the importance of multi-factor authentication, yet many companies fail to implement it. Companies are digitizing operations and taking on greater liability for storing customer data, making MFA important to your security.
Today, authentication based on usernames and passwords alone is unreliable because users have trouble storing, remembering, and managing them across multiple platforms. In the quest to remember passwords, users reuse the same password increasing the risk of potential attacks.
Apart from passwords, use these methods for MFA:
● One-time passwords (OTPs): A unique one-time password sent to a customer’s mobile or email that they must enter after their password.
● Hardware tokens: Use physical devices that can generate unique codes for login in a system. Users must have this device with them when accessing any system.
● Soft Token Software Development Kits (SDKs): Developers can use OTP generation in their applications using SDKs.
● Authenticator apps: These applications generate OTPs and push notifications to verify a user's credentials trying to gain access to an application or website.
6. Use transparent data handling practices
Many companies focus on auditing and logging features on their storage systems. This helps them comply with regulatory requirements and shows their dedication to transparency in data handling practices.
When you allow users to monitor how others are using, managing, and accessing their data, it instills a sense of confidence. By doing so, you can prevent misuse or inappropriate use of data.
Data handling practices also involve controlled data sharing. This implies you don’t share personal data with third-party vendors without the user’s consent. As a result, you protect the user's information from unauthorized access.
Transparency in data management helps you avoid retaining the user’s data longer than you need. You commit to properly destroy it at the end of the lifecycle, eliminating the possibility of future attacks.
7. Give training to your workforce
With the cybersecurity short of 3.4 million professionals, the best way to ensure data security is to train your employees.
You can provide in-house training on:
● Malware,
● Social engineering
● Ransomware,
● Phishing,
● Using strong passwords,
● Ignoring suspicious emails, and
● Being vigilant when sharing sensitive information.
Many companies train their employees to identify and respond to potential security breaches. A well-educated workforce is one of the strongest pillars of your data security strategies.
8. Pair your data security with data resilience
Preventive measures are a feel-good factor in data security, but data resilience helps you stand out. Data resilience is your company’s ability to endure, recover, and adapt to data security incidents and thefts.
Having a backup system, creating disaster recovery plans, and regularly testing these measures to ensure they work are a few ways of data resilience.
Even the most robust security strategy cannot eliminate every risk. Because of this, companies are slowly placing emphasis on incident recovery and responses. Pairing your data security with data resilience protects your data from potential attacks. It also ensures your data remains accessible and recoverable during an attack.
This comprehensive approach to protecting user’s data builds trust among users and reduces malicious attacks.
Upgrade your data security
Cyberattacks have become more frequent in the past few years, requiring you to pay attention to your data security.
Strategies such as CCPA compliance, penetration testing, and data resilience are preventive measures to minimize risks and reduce the impact of cyberattacks.
Modern companies can securely wade the digital landscape by embracing the right strategies. While you may face some bottlenecks when implementing them, consider the value they will likely bring in the coming years.
Also, stay up-to-date and informed about the latest security measures and advancements in cyberspace to remain one step ahead.
Which of these strategies will help you the most? Are there any other data security strategies you use for securing your data?
