Bruteforce hashes
Exhaustive Bruteforce Configurator
This is an exciting new feature we propose to you: to customize your own Bruteforce options, thanks to our 'configurator'.
This option will allow you to choose the right Charset (Lower / upper letters, Digits, Symbols, etc.) and the Length (from 1 to 25).
Step 1. Upload your Hash(es)
Let's upload a sample MD5 hash '51841F5D5F89BBED59E7DB102889A07A' thanks to the form here.
Let's admit for this how-to that password is not found despite our wordlists and other conventional means:
Step 2. Configure a specific Bruteforce
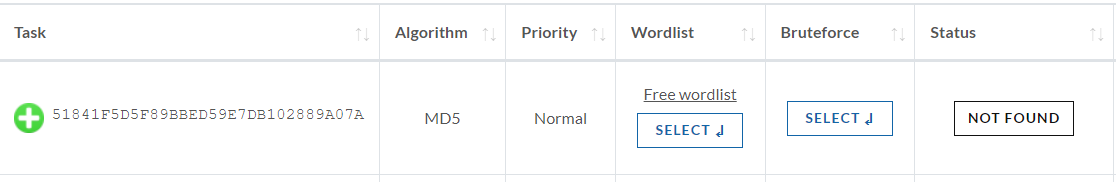
You want to run a specific and custom Bruteforce job on this hash, click on 'Select Bruteforce' buttton:
The Bruteforce Menu appears below:
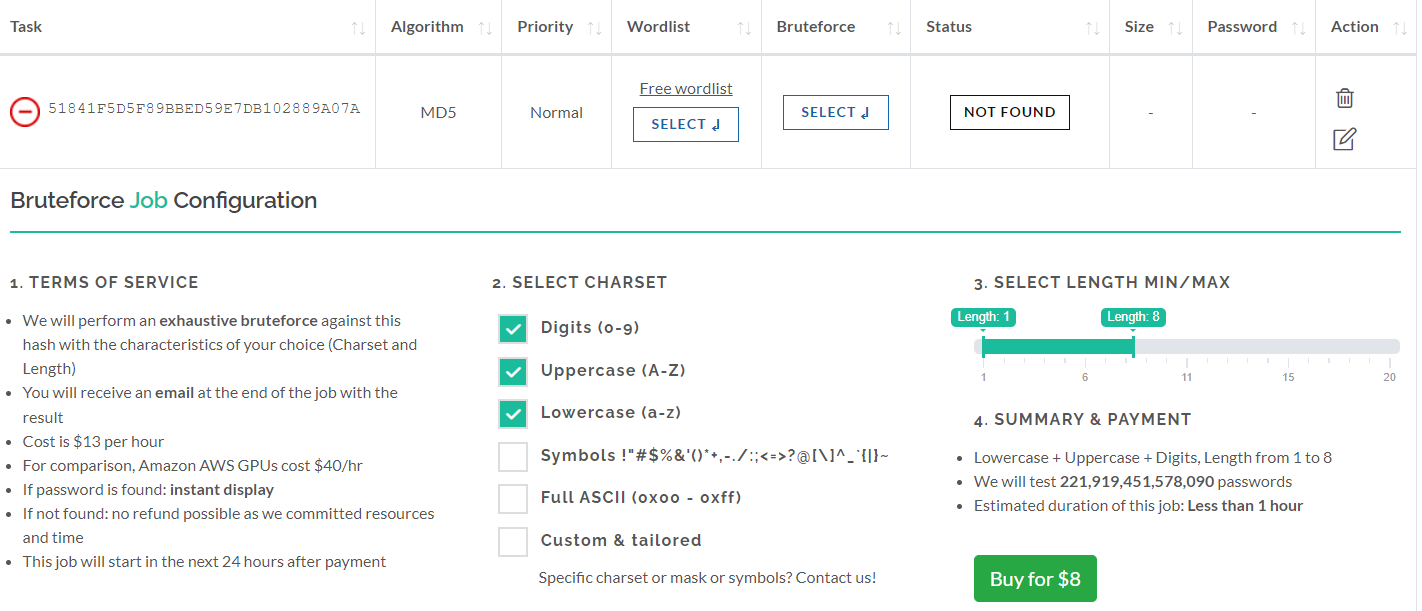
I guess the password is made up of lowercase letters (a to z) and digits (0 to 9) and length should range from 4 to 10 characters:
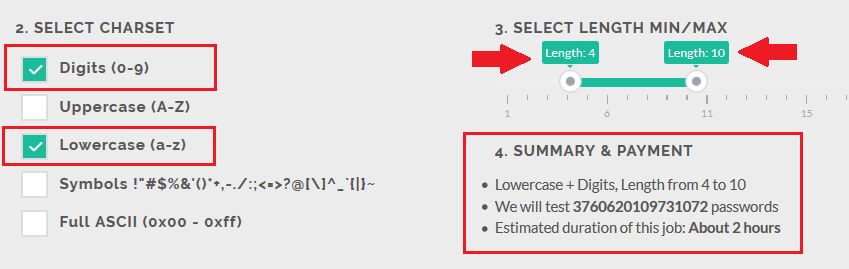
The Summary part shows:
- Charset choosen: Lowercase + Digits
- Length: from 4 to 10 characters
- Number of candidates we will test for you, in our example: 3'760'620'109'731'072 = 3.7 x 10^15 = "3 quadrillion 760 trillion 620 billion 109 million ..."
- Estimated duration of the job, which depends on the previous Charset and Length choices and the algorithm (MD5 in this example).
- Payment is required upfront.
Step 3. Follow-up
Once payment is done, we will start your specific bruteforce job.
You can follow the progress and the results just below the Configurator:
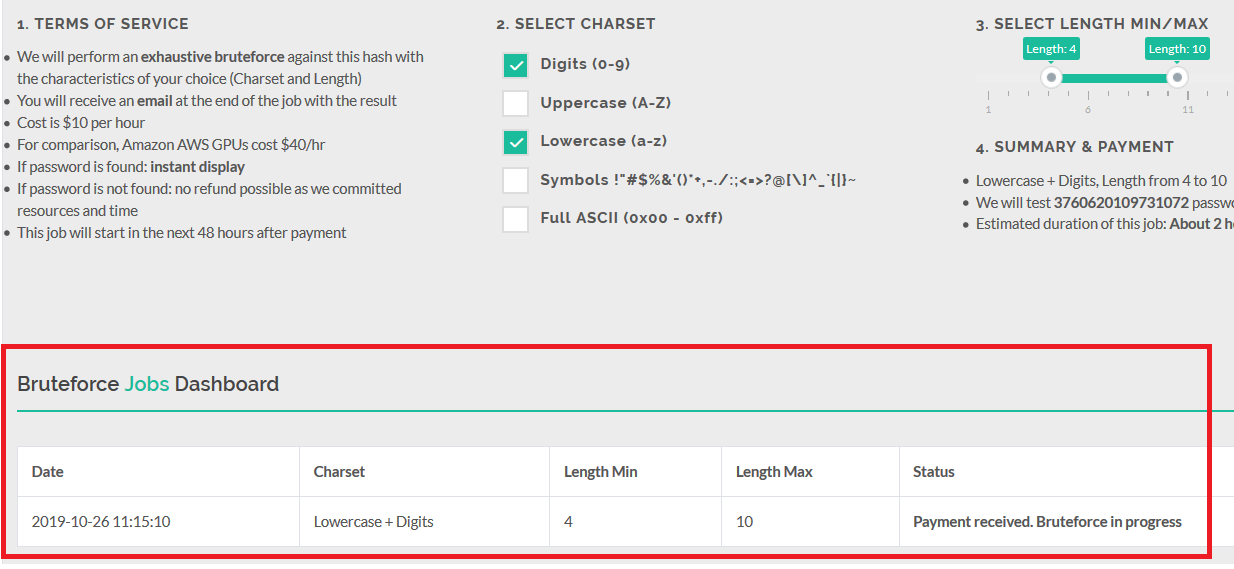
- Password is found: instant display on your dashboard, + email notification.
- Password is not found: You can try another configuration to try more and/or different charsets. No refund possible as we committed resources and time to try to recover it.
